Lab 8 | Deploying Certificates and Implementing Key Recovery
Lab 8 | Deploying Certificates and Implementing Key Recovery
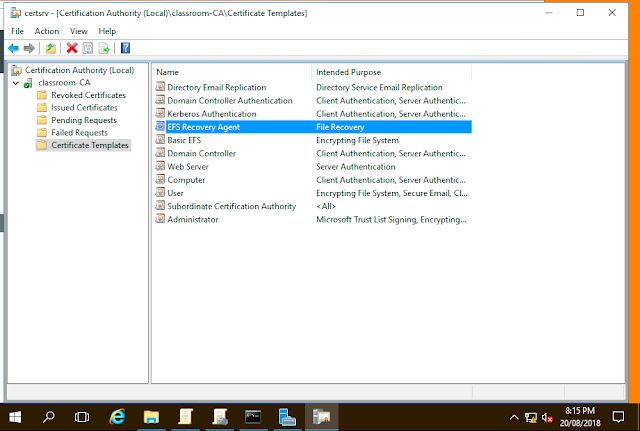
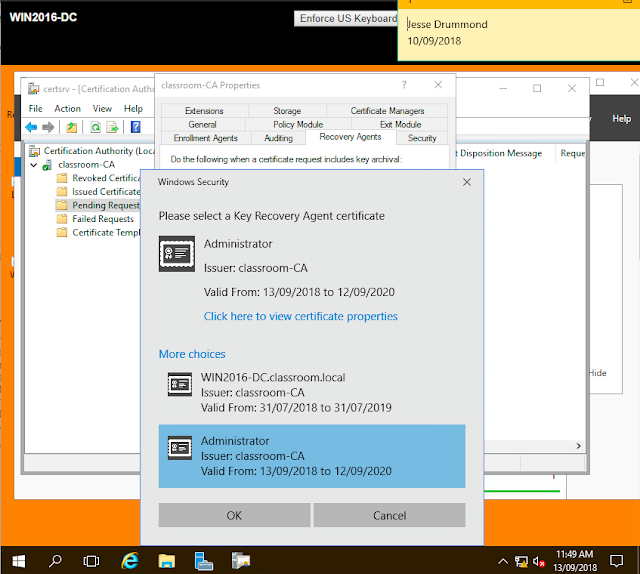
In this lab, we are experimenting with key recovery whilst also learning more about some more nuances of the certificate authority service.
First, we requested a certificate to our WIN10-WS machine from a browser console, this took some problem solving from people in the class due to the original instructions not working in Microsoft edge, it only worked within internet explorer with a specific configuration.
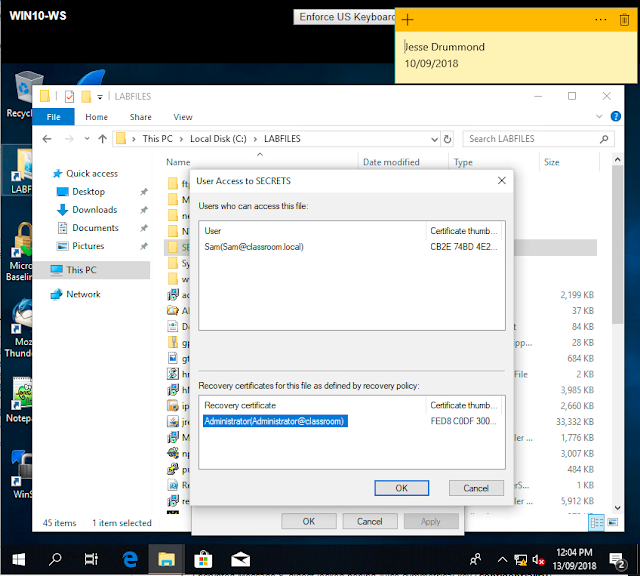
Viewing the recovery certificate thumbnails, these were noted down for later use to ensure we were still working with the correct certificate.
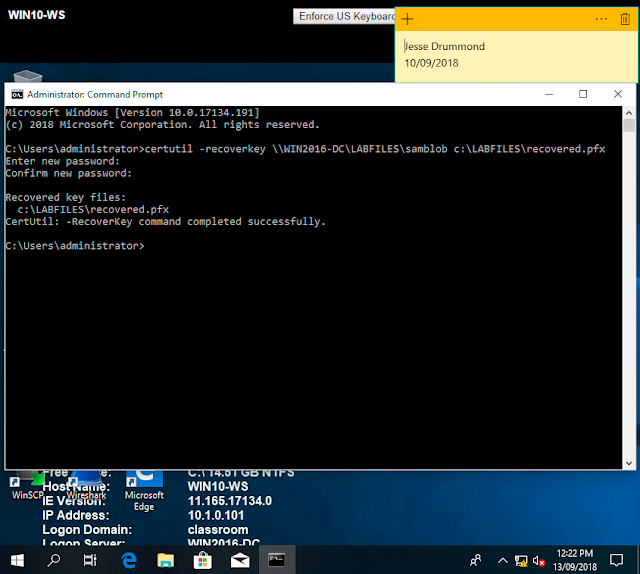
Retrieving the certificate using the serial number of the certificate
Successful recovery of the certificate file in WIN10-WS, using the password.
Successfully regaining access to the files after we deleted the certificate, we used the key recovery to reinstate the certificate that was deleted.
Lab Questions
Ex 3 | 5
Make a note of the certificate thumbprints:
Sam: CB2E 74BD 4E28 FB24 4A8F 0D49 15D3 A0BF 7BF0 BF65
Administrator: FED8 C0DF 3005 71D7 44B7 E0A0 0A34 DFC4 18CC 5CBA
Sam: CB2E 74BD 4E28 FB24 4A8F 0D49 15D3 A0BF 7BF0 BF65
Administrator: FED8 C0DF 3005 71D7 44B7 E0A0 0A34 DFC4 18CC 5CBA
Critical Thinking & Analysis
Upon reflecting on the usefulness of the key recovery agent it is apparent to me that this is mandatory if you have users encrypting important business files, if the certificate for these files is lost by any means then it may not be possible to regain access to this data again. Correctly taking measures to implement key recovery ensures that we can regain access to the certificate if we require, although the process is not simple and should be locked behind a secure & strong password it is possible if required.
Certificates, in general, allow us to greatly increase the security of our systems by only allowing access to certain network elements if the correct certificate has been distributed by the certification authority. It was noted in the lab that it is not best practice to install a certification authority on a dc with other domain services such as active directory, these services are best kept segregated to optimize the security of your domain environment.





Comments
Post a Comment