Lab 5 | Using Network Scanning Tools 2
Lab 5 | Using Network Scanning Tools 2
In this lab, we further explore the capability of network scanning tools that monitor the communications between hosts running on our local network.
For this lab to function correctly we need to use a virtual router that has 'promiscuous' mode enabled which allows one port to read all the traffic that is going through the router it is connected to. This is also commonly known as port mirroring.
We have used the application 'Wireshark' to inspect the traffic that we are picking up, using this we can see the content of frames including the information at each layer which proves to be rather extensive in that we can see the contents of the packet entirely. Pictures above is a DHCP frame.
Above we are following the content stream of an SMB2 frame, this interface shows the communication between the two hosts which is defined by the blue & red colouring. This allows us to observe the exchange between two hosts when transmitting a packet. SMB2 uses the TCP protocol which essentially means that the two hosts need to 'handshake' each other to ensure the content transmitted arrives in the same form that it was sent without any content missing.
Our next exercise in this lab had us setting up a file share with a 'confidential' file inside it. Due to inherent vulnerabilities, we were able to retrieve the content of this file by sniffing it with wireshark, as long as we know which frames to inspect in-depth it is a rather trivial exercise, these types of files need further security applied to them in order to maintain a state where the content can not be read by people sniffing into the network traffic.
The next exercise demonstrated a scenario of a disgruntled administrator attempting to exfiltrate a confidential file out of the system by installing a backdoor that facilitates this.
We attempted to access the file through ncat to start with but found that we were unable to due to already set security constraints, we worked around this by adding a firewall rule that allowed us to complete the following tasks, in which we monitored the current TCP connections.
Following this we use ncat to transfer the file to WIN10-WS, in our WIN2016-DC machine we can observe this transfer through the port our firewall rule opened earlier.
Lastly, we hop over to wireshark where we can observe the packets of the file transfer that took place. We can view the packets down to the file content.
Below is a second run of using ncat to view confidential.txt file contents. I did a second run in order to gain a better understanding of the process and to improve my blog content.
Lab Questions
Ex 3 | 10
Open a Run dialogue and enter \\WIN2016-DC. Does the secret$ share appear?
It does appear, this is due to us specifying the exact path to the shared folder, if a $ is at the end of a share then it is not possible to navigate to this share without putting the fully qualified address.
It does appear, this is due to us specifying the exact path to the shared folder, if a $ is at the end of a share then it is not possible to navigate to this share without putting the fully qualified address.
Ex 3 | 16
Ex 3 | 19
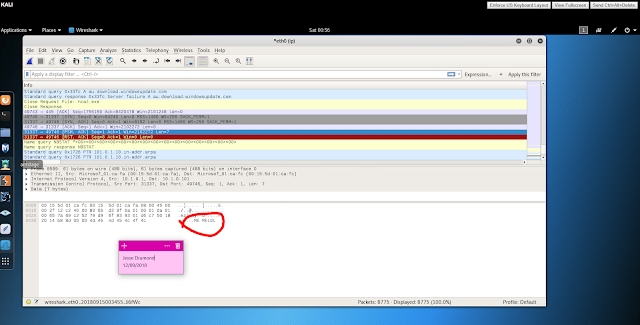
Does the secret message appear in the data?
Yes, pictured below.
Yes, pictured below.
Ex 4 | 4
Can you think why this doesn't work?
It appears that this does not work due to WIN10-WS not being able to communicate with WIN2016-DC in the correct manner for ncat to function correctly, I am still able to ping WIN2016-DC so I can tell it is a specific port or protocol that needs to be used in order for this to work properly.
It appears that this does not work due to WIN10-WS not being able to communicate with WIN2016-DC in the correct manner for ncat to function correctly, I am still able to ping WIN2016-DC so I can tell it is a specific port or protocol that needs to be used in order for this to work properly.
Ex 4 | 7
Critical Thinking & Analysis
From this lab, it was demonstrated how it is possible to detect the illegal exfiltration of files if you have the correct setup in place, although this requires active action and does not help if you learn about an attack of this sort prior to it happening. I suspect there may be programs that can be set up to continuously listen for the unwanted transfer of files through vulnerable ports by methods that are not contemporary to the business environment.
During the Lab I could not get ncat to work on WIN10-WS, I found out this was due to it not being installed on the system, I used the share we already set up in the lab to transfer the file from the DC to WIN10-WS, I then installed it and from there the cmd commands worked as intended.
These types of tools are easy to detect in practice so it is not anywhere near this simple of a process to be able to read file contents unless you are attacking a system that has minimal security and is looked after by someone who is not knowledgeable about their system.
It would be vital for someone that is employed in a company to know the basic requirements to stop trivial attacks like this, I can imagine it being as simple as having the right settings in your network and possibly some sort of monitoring software if required. If a sysadmin followed standard security protocols I think this sort of attack would be ineffective.
These types of tools are easy to detect in practice so it is not anywhere near this simple of a process to be able to read file contents unless you are attacking a system that has minimal security and is looked after by someone who is not knowledgeable about their system.
It would be vital for someone that is employed in a company to know the basic requirements to stop trivial attacks like this, I can imagine it being as simple as having the right settings in your network and possibly some sort of monitoring software if required. If a sysadmin followed standard security protocols I think this sort of attack would be ineffective.












Comments
Post a Comment