Lab 2 | Malware Types
Malware Types
In this lab, we performed an exercise that deploys a trojan virus that we then exploited & then consequently prevented using Microsoft defender and by setting an inbound firewall rule to patch up the vulnerability.
Our machines came with the virus inside a folder ready for us to install, after installing said virus we reviewed the firewall inbound rules(pictured below) as well as the task managers currently running processes, at this stage I could not spot the problem although I had my suspicions about 'nc.exe' which later was confirmed to be the culprit exe file that our virus installer had installed without our knowledge, as for the anomaly in the inbound firewall rule, I did not spot this until later on in the tutorial when we were instructed to delete the rule "Service Firewall" which was being implemented by the virus as a rule that allowed our WIN07 virtual machine to connect using PuTTy.

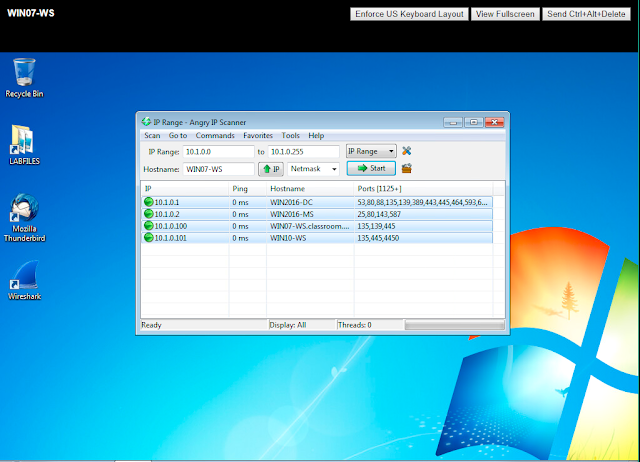
Below is us on the other machine that is acting as the host who is exploiting the backdoor the virus has opened up for us, using this 'Angry IP Scanner' program we are scanning the network we are on for available computers we can attempt to connect to.
After configuring some settings within this program to search for a specific range of ports, seeing if any are open we can see that all four machines had open ports, although port 4450 on machine WIN10-WS is the one we are looking for, we know that the virus has opened this port for us which will allow us to connect to it and exploit its vulnerability.
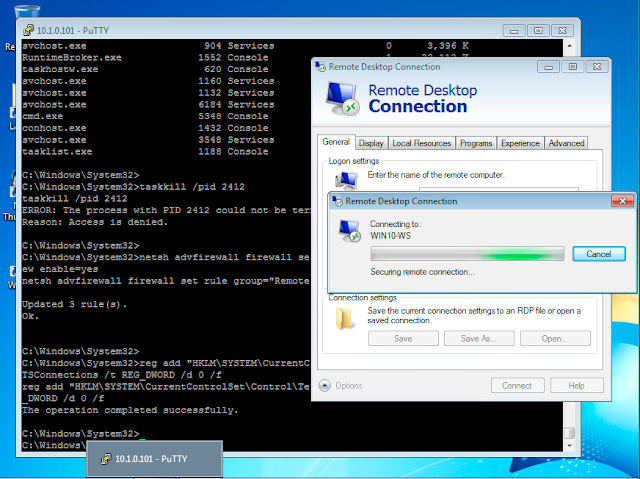
Once gaining access to the infected PC's command line through putty this allowed us to execute a wealth of commands without the infected user's knowledge, so far throughout this process, we have managed to gain access to the infected pc's command line and execute malcious commands.
Within this script that the virus installed, we can see that there is code that adds a firewall rule to our computer allowing us to access it from our other PC.
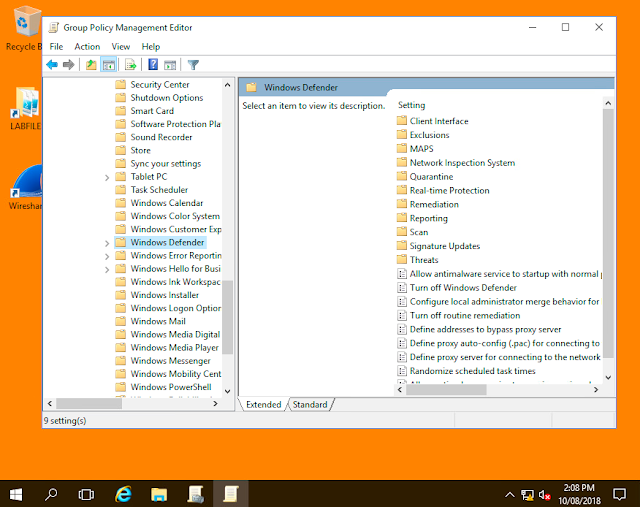
Using group policy we can apply rules to the computers in our domain, in this exercise we used a group policy that enables windows firewall and disables the option to disable it as well, taking control away from the hosts pc which takes away the ability for the virus to turn off the host's firewall.
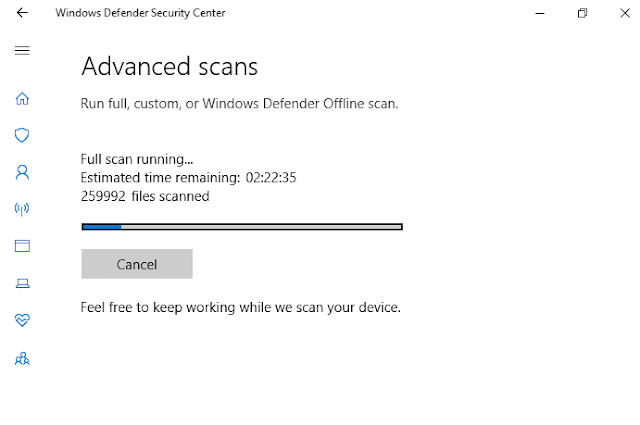
Once we enabled windows defender again and execute a scan we can notice that it picks up a virus threat, we found out that windows firewall cannot actually disable the virus from functioning and following this we had to manually implement a firewall rule that blocks netcat from executing at all.
Lab Questions
Ex 1 | 8
Can you spot anything unusual?
The first thing that stuck out to me was the 'nc' entry which appeared abnormal due to tasks typically not having such a short name. I am also moderately familiar with task manager from personal experience.
Ex 1 | 10
Can you spot anything unusual?
I could not spot anything unusual in here, I suspect that this is due to my level on unfamiliarity with reviewing the event viewers contents. This highlights how it can be difficult for somebody to know if their system is comprimised if they are not already familiar with what is normal within these interfaces (task manager & event viewer etc).
Ex 1 | 12
Can you spot anything unusual?
Similar to the event view initially I was not able to spot anything unusual although after progressing through this Lab I was able to recognize where the culprit entry was. 'Service Firewall' was the entry in question that was allowing TCP connections to the system.
Ex 2 | 15
Look at the other open ports on all four VMs - how many of them can you identify?
I recognized 443, 445, 80, I am not sure was the responsibility of these ports are exactly except that I know one or two of them related to an email protocol. The domain controller has significantly more open ports than the other PC's, I suspect this is because it provides many services to the network.
Ex 5 | 7
Despite the notification of "protected" status, what major problem is there with this antivirus deployment?
I am not sure but I suspect that the problem with this virus protection is that we only have one layer of defence, being windows defender. Otherwise it could possibly be that we have enabled virus protection after the virus has infected our system.
Critical Thinking & Analysis
This lab has shown me a valuable perspective on the side of the exploiter and exactly how the 'hacker' got access to the vulnerable PC, through the installation of a simple little program we were able to install a keylogger, although this was not without the users awareness because it had to log them off in order for us to get into the account we created. It is possible to get in without the users' knowledge using a more in-depth kind of exploit.
Another thing I have learnt from this exercise is that it is hard to recognize if you are infected by malicious software unless you know exactly where to look or if you have proper anti-virus measures already in place. While inspecting the inbound firewall files as well as the event log I could not recognize what the malicious software had done considering that I did not have prior knowledge of what was normal and what would look out of place.
Another thing I have learnt from this exercise is that it is hard to recognize if you are infected by malicious software unless you know exactly where to look or if you have proper anti-virus measures already in place. While inspecting the inbound firewall files as well as the event log I could not recognize what the malicious software had done considering that I did not have prior knowledge of what was normal and what would look out of place.






Comments
Post a Comment